
The ECDSA signature method is used to sign a message with a private key. So rather than sharing the signature, could we give a share of the signature to a number of nodes, and who must come together to share the signature. We will only be able to recover it if enough hosts come together to share their shares. In this case, we will use Shamir Secret Shares (SSS) for which we have n shares, and where we can recover the share using t nodes:
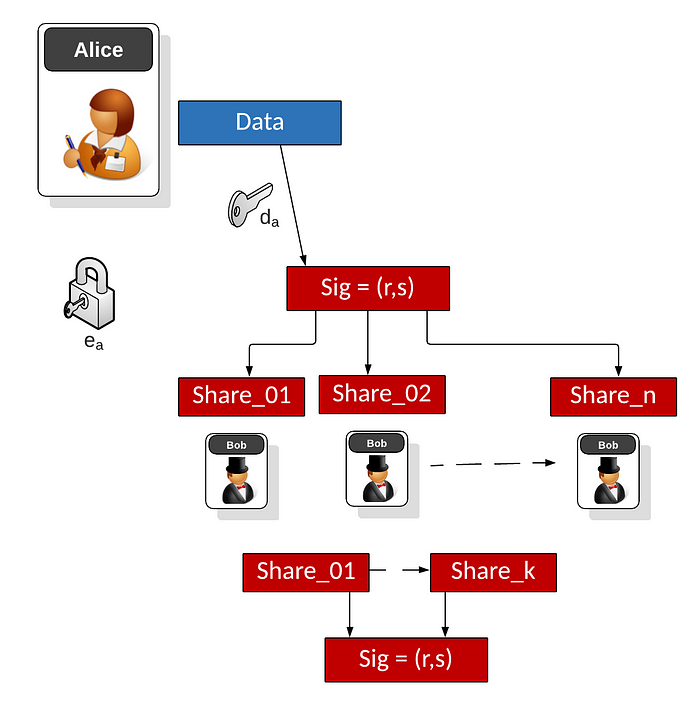
For ECDSA, Alice signs the message with the following:
- Create a hash of the message e=HASH(m).
- Let h be the Ln be the leftmost bits of e, Ln has a bit length of the group order N.
- Create a random number k which is between 1 and N−1.
- Calculate a point on the curve as (x_1,y_1)=k×G
- Calculate r=x_1(modN)
- If r=0, go back to Step 3.
- Calculate s=k^{−1}(h+rdA)(modN).
- If s=0, go back to Step 3.
- The signature is the pair (r,s)
Bob will check with:
- Create a hash of the message e=HASH(m).
- Let h be the Ln…
