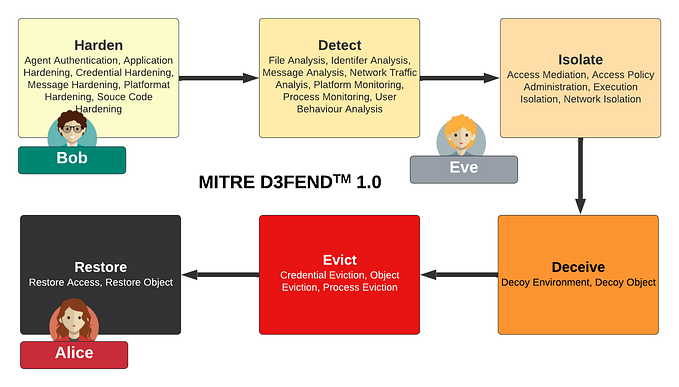
Password Authenticated Key Exchange (PAKE) is generating a good deal of interest, and a secret held only by Bob and Alice could be used to generate secret connections between them. One of the most convenient of these is a password, but it could as easily be a random nonce.
Encrypted Key Exchange (EKE) was created by Steven M. Bellovin and Michael Merritt [1] and uses a shared password to encrypt the Diffie-Hellman key exchange. In this method, an initial encryption key is generated from a shared password, and which is then used to generate a session key through an encrypted Diffie-Hellman handshaking process:

Initially, Bob and Alice agree on a password and then generate an encryption key from a hash of the password (P). Alice initially creates a secret value of a and then computes:
This is then encrypted with the P key:
Bob receives this and can recover:
Bob then create a random value b and then computes a new key of:
He encrypts with this P:
Bob then creates a new challenge (c1) and encrypted with the new key (K):
These two values are sent to Alice, and with the first part she computes the new shared key of:
She can use this to then decrypt EK(c1) to recover the challenge (c1). Alice then creates her own challenge (c2) and appends to c1 and encrypts with the new key:
The following shows an overview of the method:

Bob then decrypts and recovers both c1 and c2. The following is the code [here]:
import sys
import random
import hashlib
from aes import encrypt, decryptfrom Crypto.Util.number import getPrime
from Crypto.Random import get_random_bytes
from Crypto.Hash import SHA256from Crypto.Protocol.KDF import PBKDF2
import binasciiprimebits=64
secret="Hello"if (len(sys.argv)>1)…